Discover how to easily setup and use lighthouse proxy with common tools.
Why do we need Lighthouse?
- Centralized Traffic: All your tool-generated traffic is routed through a single point for compliance.
- Header and Traffic Tracking: Automatically adds necessary headers to requests for tracking and authorization.
- Accountability: Logs all interactions, ensuring you’re covered in case of disputes or issues.
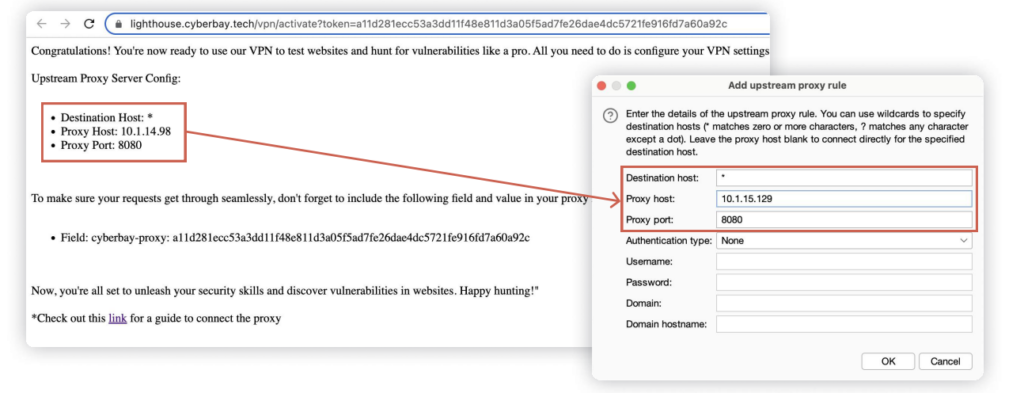
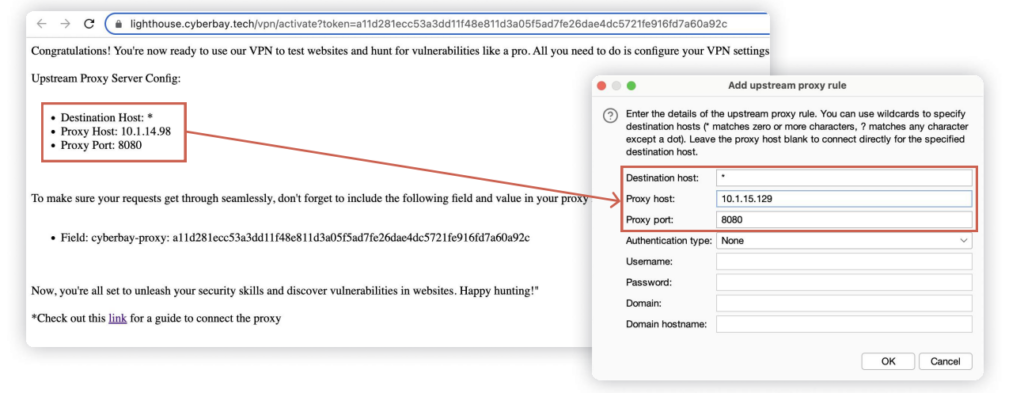
Lighthouse Setup Guide
Follow the instructions at https://cyberbay-hosting-images-public.s3.ap-southeast-1.amazonaws.com/blob-documents/lighthouse/vpn_user_guide.pdf . Retrieve the cyberbay-proxy, lighthouse host, and lighthouse port from the link and replace the header accordingly in the following commands.
Use Lighthouse with a Tool and Debugging Via BurpSuite
When using Lighthouse, routing tool traffic through Burp Suite allows you to debug requests and responses in real time. This setup is useful for troubleshooting malformed requests, analyzing responses, and fine-tuning payloads. Burp Suite acts as an intermediary proxy between your tool and Lighthouse.
1. Configure Burp Suite to Use Lighthouse as an Upstream Proxy:
- Go to Proxy > Options > Upstream Proxy Servers in Burp Suite.
- Add the following details:
- Host: <Lighthouse Host>
- Port: <Lighthouse Port>
2. Run Your Tool with Burp Suite as a Proxy:
- Use http://<BurpSuite Host>:<BurpSuite Port> (default Burp Proxy) as the tool’s proxy setting.
3. Inspect and Debug in Burp Suite:
- Open the HTTP history tab to view requests.
- Check headers, parameters, and responses.
- Use Repeater for testing modifications in requests.
Use Lighthouse with a Tool that Does Not Support Custom Headers BurpSuite
When a tool does not support adding custom headers like cyberbay-proxy: <cyberbay_proxy_id>, you can use Burp Suite as an intermediary proxy to inject the required header into outgoing requests. This allows the tool to work seamlessly with Lighthouse while staying compliant.
1. Configure Burp Suite to Use Lighthouse as an Upstream Proxy:
- Open Burp Suite > Proxy > Options > Upstream Proxy Servers.
- Add Lighthouse as an upstream proxy:
- Host: <Lighthouse Host>
- Port: <Lighthouse Port>
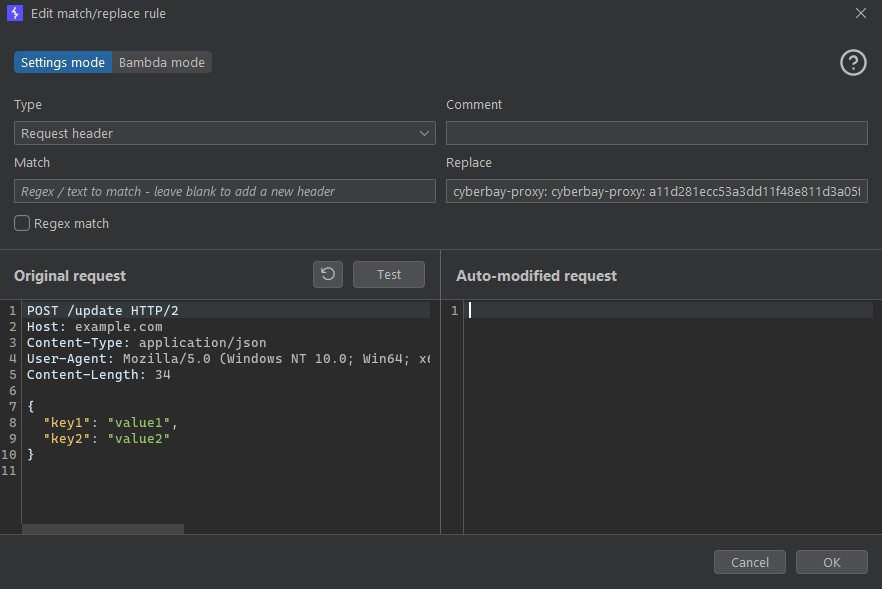
2. Set Up Request Header Modification in Burp Suite:
- Go to Proxy > Options > Match and Replace.
- Click Add and configure:
- Type: Request header
- Match: Leave empty (applies to all requests).
- Replace: cyberbay-proxy: <cyberbay_proxy_id>
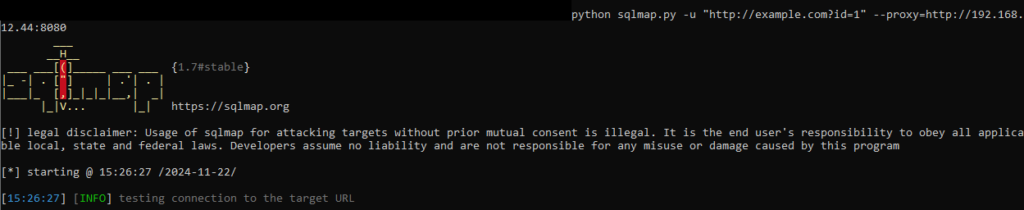
3. Run Your Tool with Burp Suite as the Proxy:
- Use http://<burpsuite_host>:<burpsuite_pro> as the proxy for your tool.
4. Inspect and Debug in Burp Suite:
- Verify in the HTTP history tab that the cyberbay-proxy header is being added to all outgoing requests.
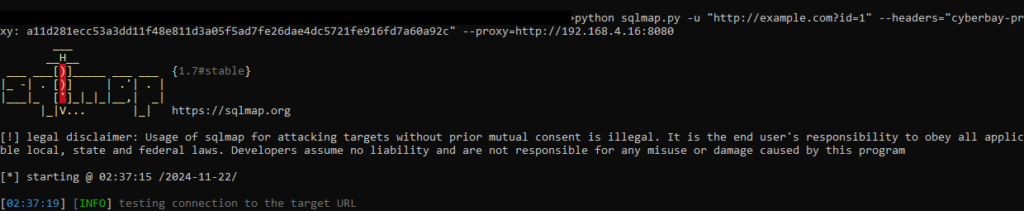
Use SQLMap with Lighthouse
Lighthouse integrates seamlessly with SQLMap for testing SQL injection vulnerabilities. SQLMap can send its requests through Lighthouse, ensuring compliance with program rules while identifying database vulnerabilities.
To run SQLMap with Lighthouse:
sqlmap -u "http://example.com?id=1" --headers="cyberbay-proxy: <cyberbay_proxy_id>" --proxy=http://<lighthouse_proxy>:<lighthouse_port>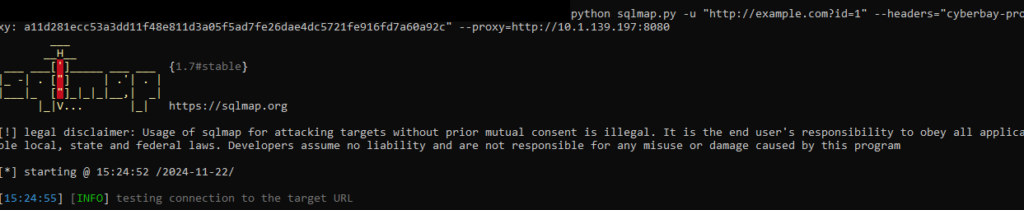
Use Nikto with Lighthouse
Nikto is a web server scanner that identifies security issues. When used with Lighthouse, Nikto’s scans remain within the legal scope and are traceable.
To run Nikto with Lighthouse:
1. Follow the steps in “Use Lighthouse with a Tool that Does Not Support Custom Headers BurpSuite” Section
2. On step 3, run Nikto with Burp Suite as the Proxy:
nikto -h http://example.com -useproxy http://<burpsuite_host>:<burpsuite_port>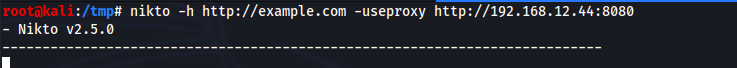
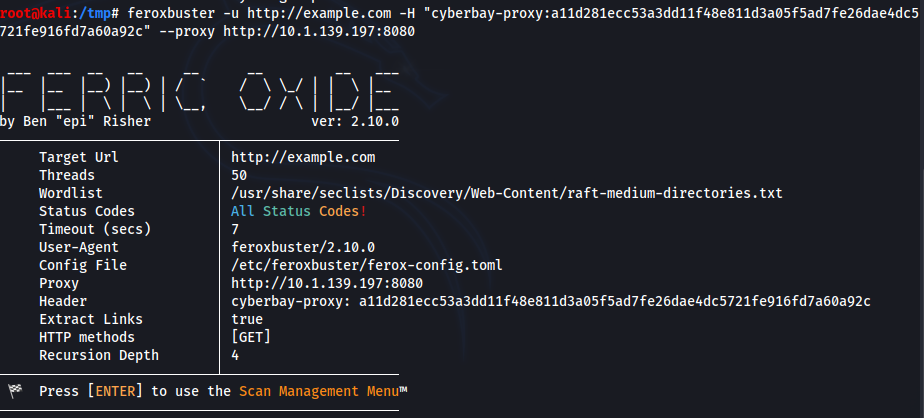
Use Feroxbuster with Lighthouse
Feroxbuster is a directory brute-forcing tool that can enumerate web directories. Using it with Lighthouse ensures scans remain scoped and auditable.
To run Feroxbuster with Lighthouse:
feroxbuster -u http://example.com -H "cyberbay-proxy:<cyberbay_proxy_id>" --proxy http://<lighthouse_proxy>:<lighthouse_port>