Create missions in the Cyberbay Corporate Portal is essential for defining specific tasks related to security testing and management within your organization. This guide will provide step-by-step instructions on how to effectively create missions, ensuring that your security initiatives are structured and targeted. Follow these steps to streamline the process of setting up missions tailored to your company’s security needs in the Cyberbay Corporate Portal.
- Log in to the Corporate portal and click the “Bounty Mission” option.
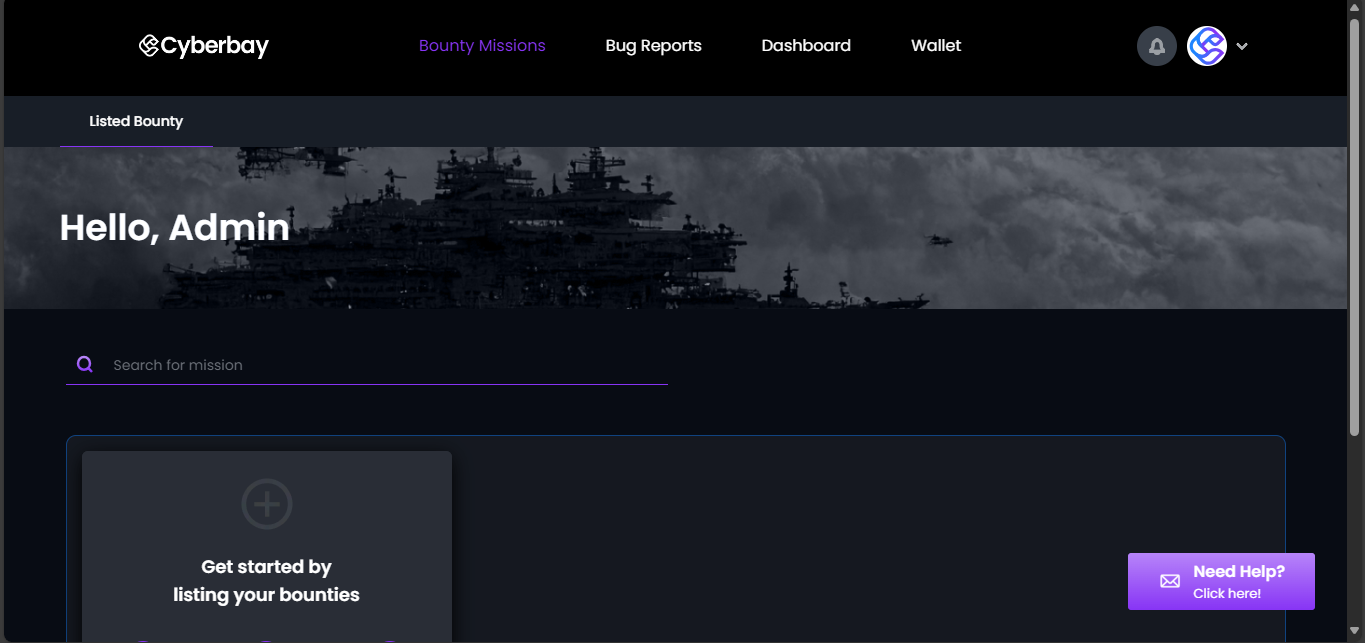
- Scroll down and click on the “START A NEW BOUNTY” option.
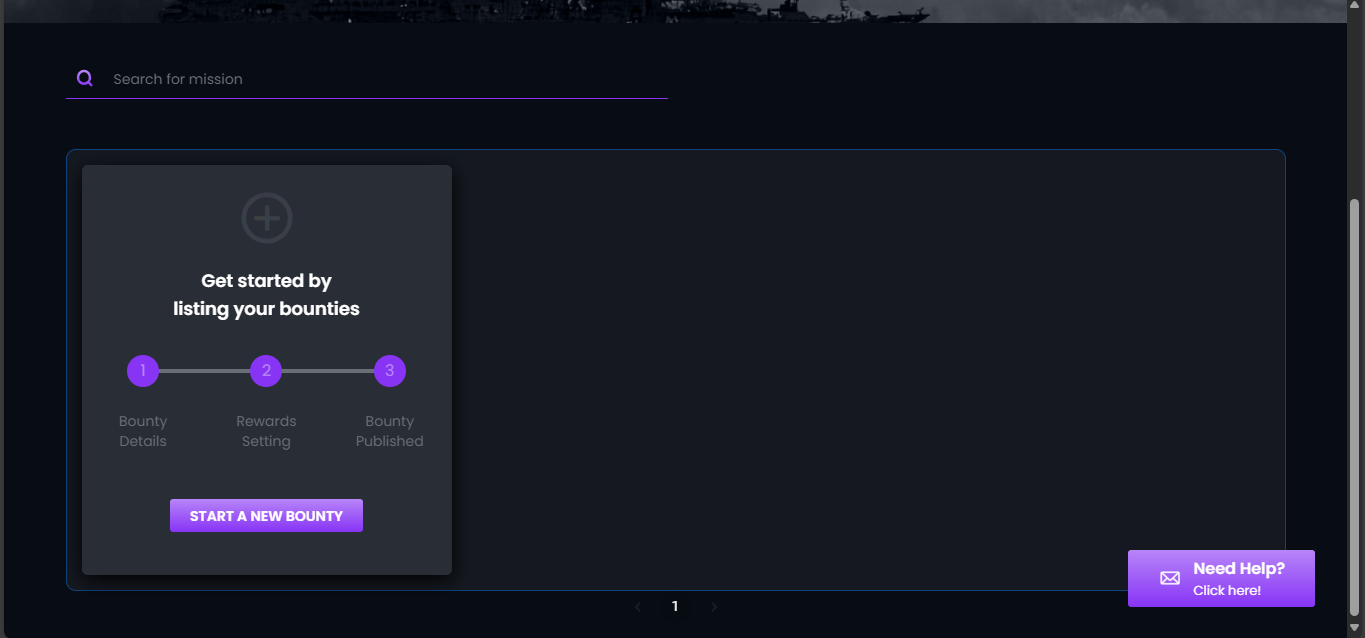
Within the START A NEW BOUNTY, you can easily update the following settings:
- Bounty Details
- Set Up Targets
- Rewards Setting
- Review Terms
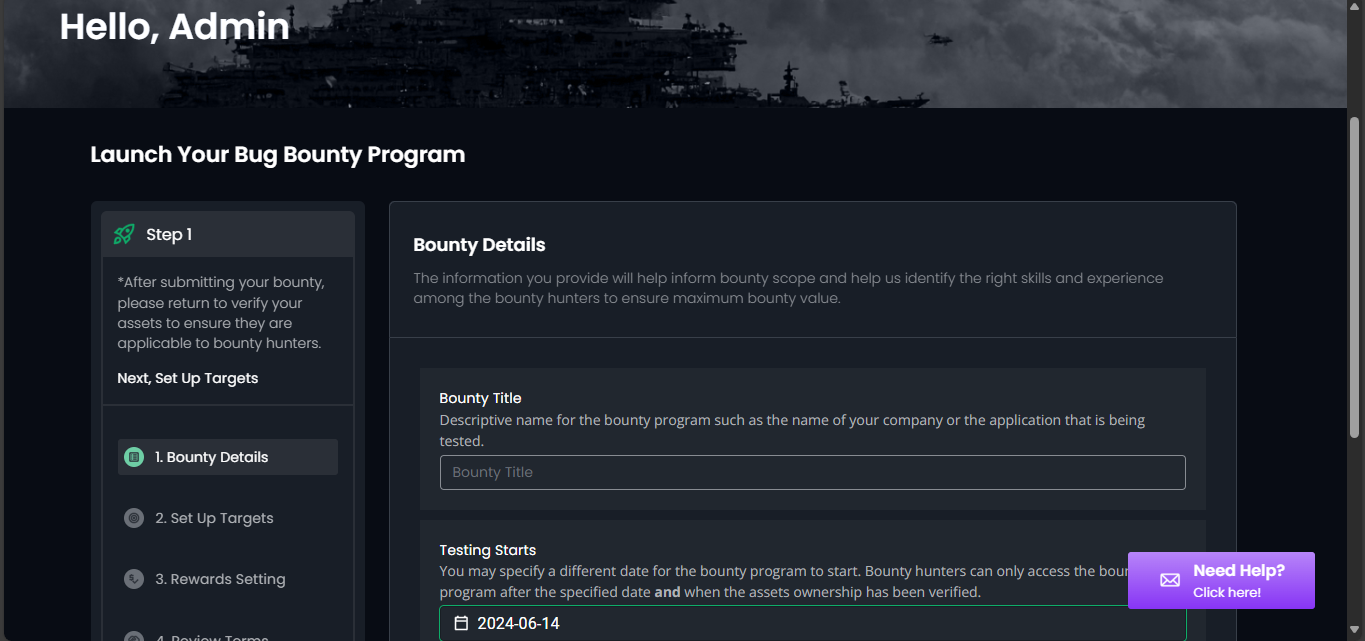
Step 1: Fill in Basic Bounty Details
Bounty Title: This will be the name displayed on the Cyberbay platform.
Testing Start Date: Specify the start date for your bounty mission. Hunters can only access the details of your mission after this specified start date.
Testing Time Range: Indicate the earliest and latest times hunters can begin their testing on a daily basis. Hunters are not allowed to access your websites or perform any testing activities outside this time range.
- Click “NEXT” to proceed.
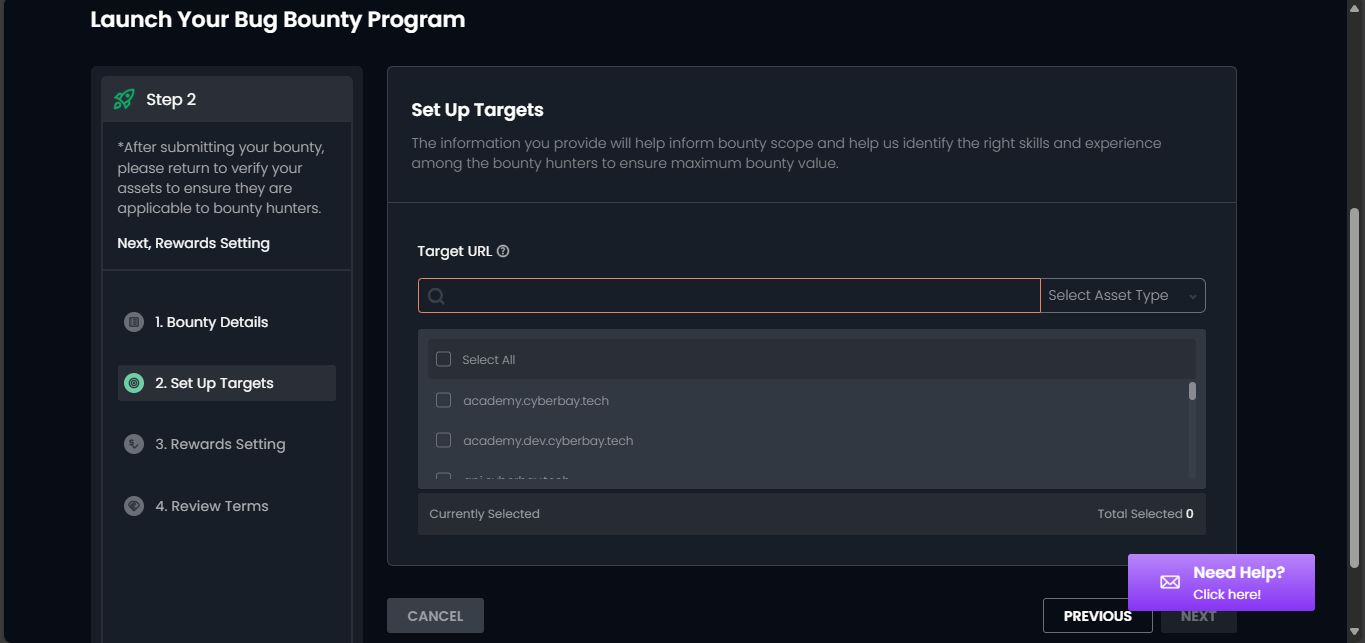
Step 2: Scope Definition – Set up Targets to Include in Your Mission
- In the “Target URL” field, enter any domains or subdomains you wish to include in the mission. Select the domains you want to test by ticking the checkboxes (we recommend selecting all).
- For newly added domains, our platform will conduct an AI scanning to discover all subdomains under the main domain. Please note that this process may take some time.
- For assets without checkboxes, it indicates that the target is currently active in other bounties and cannot be added to this mission. You must remove the targets from other missions to include them in this one.
- Please review the total assets, which indicates the number of assets to be included in the mission. You must verify the ownership of the assets you wish to include for them to be visible on the Cyberbay platform.
- Click “NEXT” to proceed.
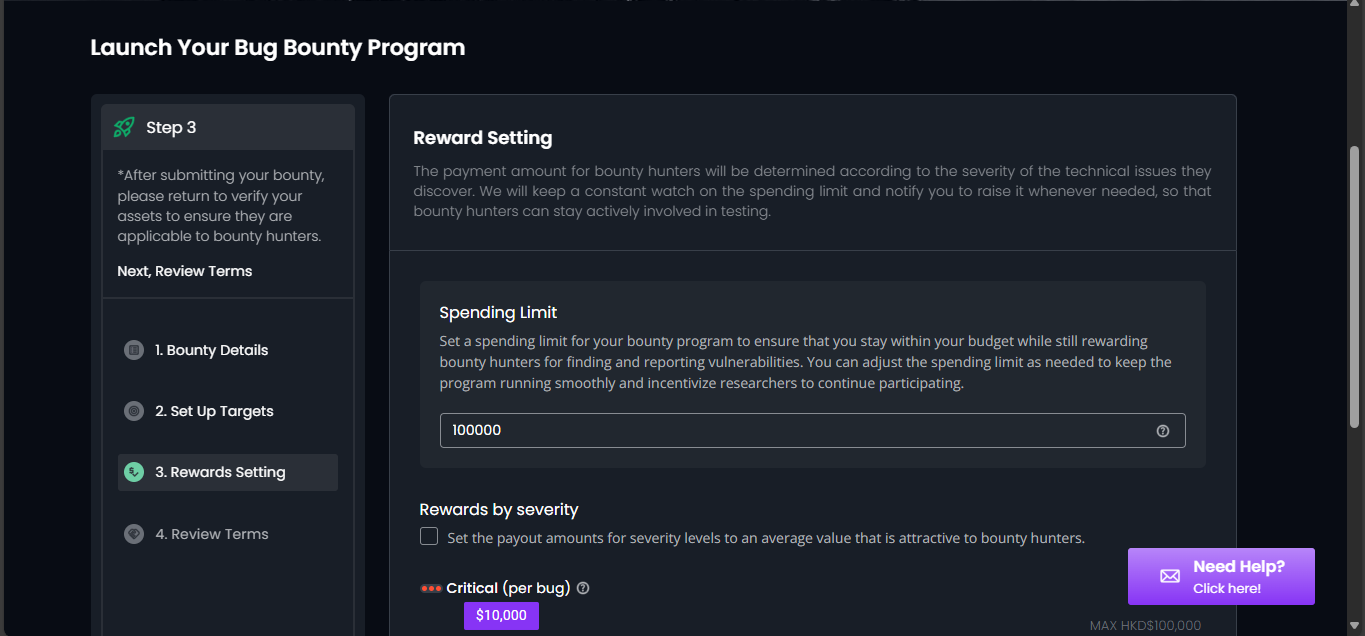
Step 3: Reward Setting
- Set the payout amounts for severity levels to attract bounty hunters. The payment amount for hunters will be determined according to the severity of the technical issues they discover.
- Click “NEXT” to proceed.
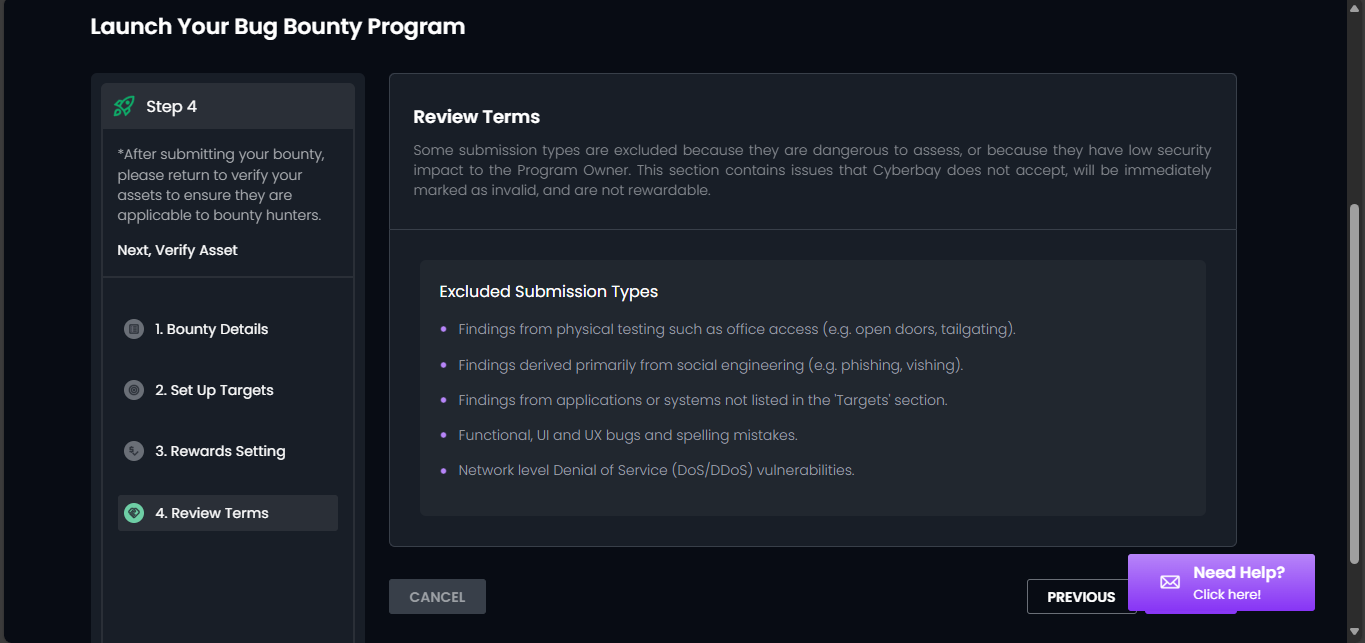
Step 4: Review Terms
- Review the exclusion of certain submission types due to safety concerns or low security impact.
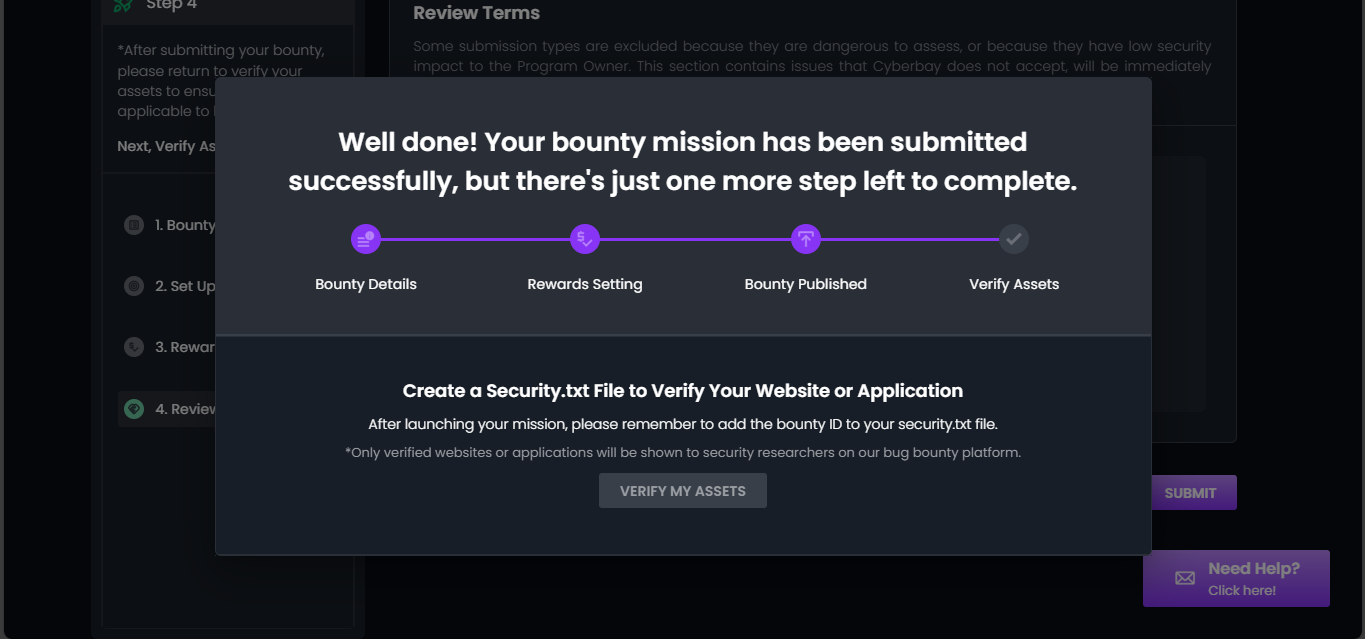
Step 5: Submit the Bounty and Verify Your Assets
- Click “Verify My Assets” to proceed. Only verified websites or applications will be shown to bounty hunters on Cyberbay’s platform.
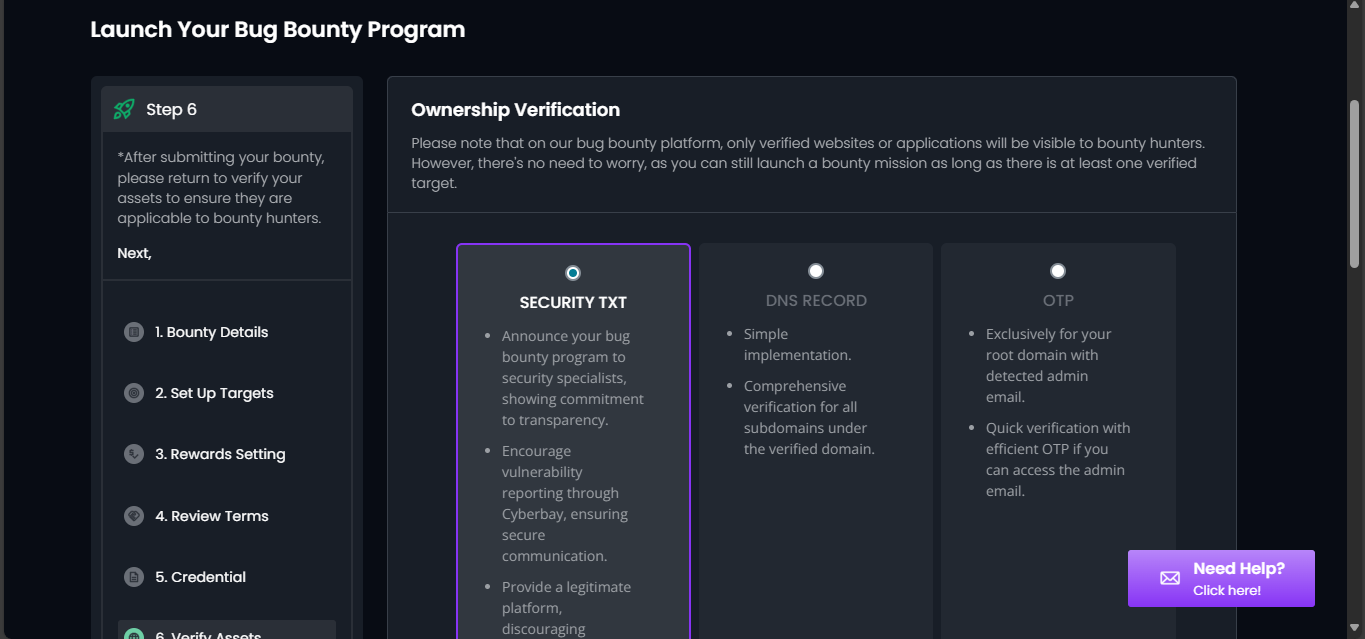
- You can edit the bounty details, but the mission will not be available to hunters until you verify ownership and reach the start date.
- To verify ownership, you can choose one of the following methods: Security.txt, DNS record, or set up OTP (only for your root domain with a detected admin email).
Step 6: Add Credentials (if any)
- Ensure you have the necessary credentials ready before your mission starts to allow hunters to conduct thorough testing of your assets.
Step 7: Successful Mission Launch
- Your mission card will display a schedule tag if it hasn’t reached the start date yet.
- Once your mission has begun and all asset ownership has been successfully verified, your mission card will show an active tag.
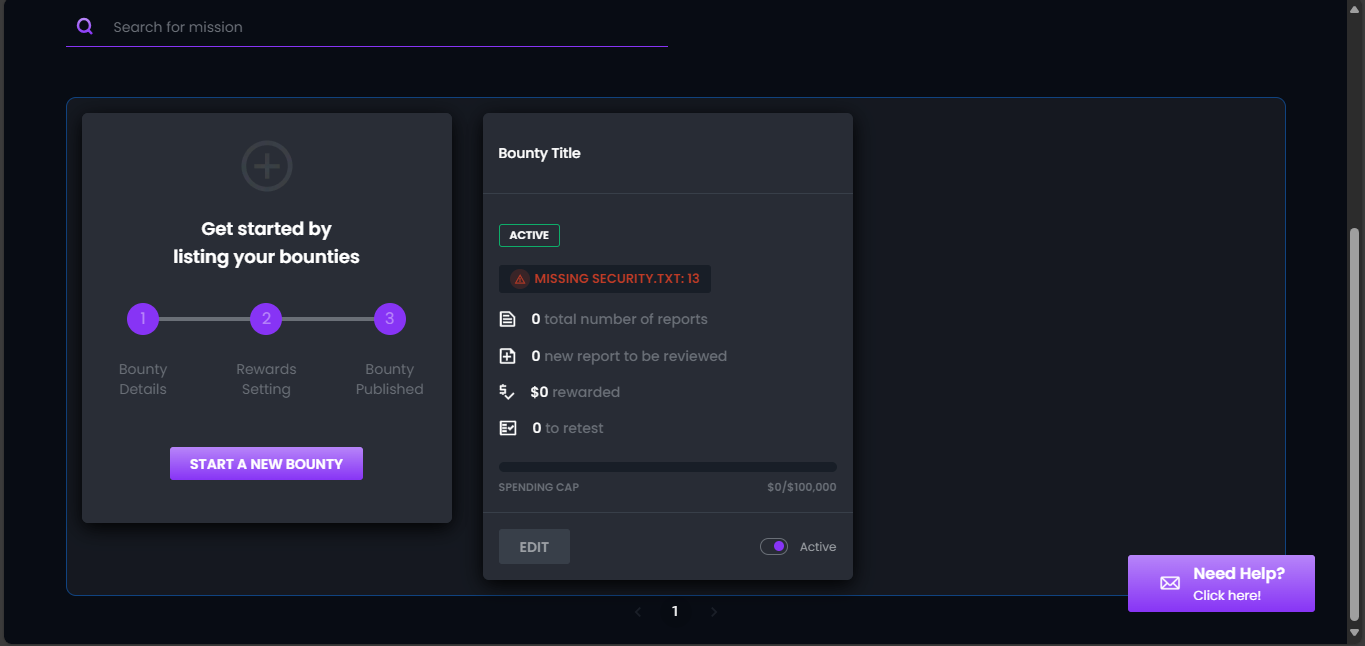
- If the mission has not yet reached its start date and there are unverified assets, your mission card will show a schedule tag and a red “missing security.txt” tag.
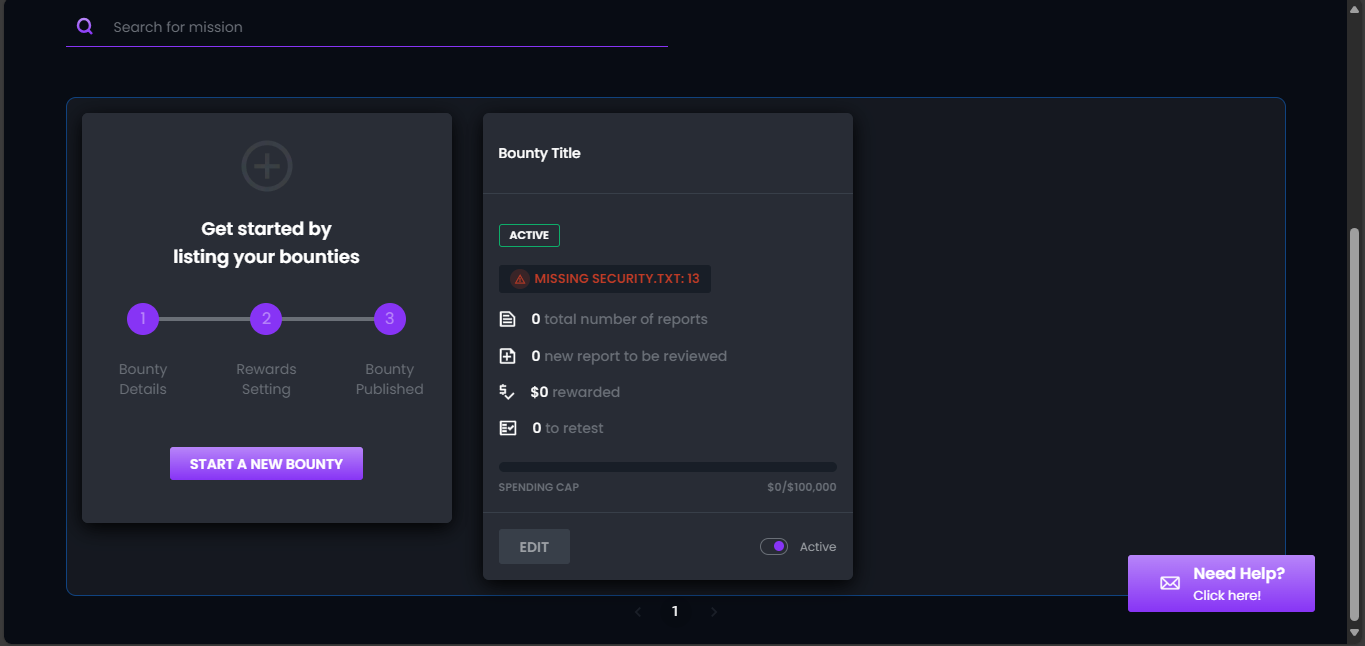
- Once your mission begins, your mission card will feature an active tag and a red “missing security.txt” tag if there are assets that still need verification despite at least one ownership being successfully verified. Hunters will have access to the mission starting on the scheduled date, with only verified assets visible to them.



